By
Philip Churchill on November 19th, 2007
Some Windows Home Server users have been experiencing data corruption issues in scenarios where data files that contain alternate NTFS data streams can potentially become corrupted when copied to shared folders on WHS.
This is a major issue that Microsoft are currently testing and have said that it will be fixed as part of one of their next updates. However until that update is available, they advise not to store data files with ADS on the shared folders or not to use applications that use data files that contain alternate data streams when those data files reside in a shared folder on a Windows Home Server-based computer.
Basically ADS (alternate data streams) is a “hidden” data that gets attached to a file residing on an NTFS partition that is not normally accessible by the user. The most frequent uses of ADS for home users are when IE6/7 downloads a file, it will attach an ADS that “tags” it as downloaded content so when you try to open the file, it shows you a security warning. Windows Photo Gallery can use them to append metadata to AVI files.
So, what can we do. Well first we need to find out if any of the files contain ADS. In their KB Article Microsoft recommend using a command line utility called Streams, some have also recommended the Windows based ADSTools but this only scans one folder at a time where as, the alternative tool ADS Spy gives you the option of viewing the contents of the ADS and removing them, all within a GUI interface, which in my opinion is the best tool for the job.
Using the latest version of ADS Spy we do a full scan which scans every hard drive for ADS streams and making sure that the option to “Ignore safe system info data streams” is unchecked.
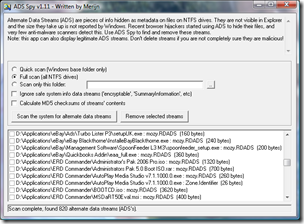
The favorites folder on my computer contained lots of ADS information about favicon, which are safe to remove but I left mine as I was not moving my favorites folder over to Windows Home Server. Some .jpg photos and Microsoft Word .doc documents had ADS data, BUT only the ones that were emailed to me. These were displayed as Zone.Indentifier files as were some .pdf documents and a lot of my .exe files and compressed .rar and .zip archives.
Thumbnail database files (thumbs.db) also had a alternate data stream and were displayed as encryptable. Outlook Express data was displayed as OECustomProperty but again I was not moving Outlook Express data, so I left these as they were. Finally Mozy.RDADS was against hundreds of files, so a quick email to Mozy (online backup solution) and you informed me that Mozy no longer uses ADS to track backed up files and the ADS could be deleted.
From all this we can tell you that it’s safe to remove the favicon stream, the encryptable stream the zone.identifier stream and the Mozy.RDADS stream if you ever had Mozy installed. Those are simple identifiers, and if removed nothing is harmed. But you should be careful about other alternate data streams. Some programs use them for things other than the simple identification that you’ve seen so far. Removing a stream from a data file used by one of those programs could corrupt the file it was on – You have been warned!







